Please, remember security is never perfect, but we can make best effort and always be informed.
Resources for Online Anonymity, Encryption, and Privacy
By Alex Meriwether | May 7th |
There are many tools available to help Internet users reach the content they seek more securely, safely, anonymously, and reliably. But the thicket of acronyms and technological terms can be intimidating to many people. What’s a VPN? How is that different than a proxy? Does “private browsing” stop my ISP from looking at my data? The complexity can cause people to throw up their hands and do nothing.
We put together this primer because inaction born out of confusion is the worst outcome. In the cat-and-mouse game against censors and snoops, there are many tools that can help, but they do very different things and they aren’t perfect. Although, there is no wholly foolproof and undetectable manner of anonymous, encrypted, private browsing, the resources we describe below are better than nothing.
Below we will map out the basics of several options available to users—including proxies, VPNs, and Tor—as well as future emerging technologies like Telex. This is meant to be an introduction to the types of tools that are available, as well as an introduction to the limitations and risks of each. We have not tested all of them, so as always, do your own research before trusting a third party with your data.
“Private Browsing” Mode in Web Browsers
How It Works: All of the major web browsers offer a “Private Browsing” function. When this function is activated, everything that the browser usually stores on the local computer—browser history, caches, cookies, download lists, form data, passwords, and other temporary files—is deleted when the browser is closed or the function is turned off. Private browsing limits what files are saved to your system so that it is more difficult for someone with physical access to your computer to trace your steps. It also makes it harder for sites to track you because their cookies are deleted.
Limitations: People mistakenly believe that “private browsing” anonymizes them to the websites they visit and makes their communications private. Unfortunately, that’s not true. Even with private browsing mode on, anyone intercepting or handling your traffic can see what you’re doing. For instance, ISPs can still record what sites you visit. And if you log into a site like Gmail, Google will still be able to associate all your actions on the site with your username, even if private browsing is enabled. Moreover, private browsing may not even stop sites from tracking you. A Stanford study determined that some sites can both determine information about visitors as well as leave behind traces on users’ systems. For instance, plug-ins installed in the browser can still track users through an independent system of cookies and temporary files. Thus, private browsing only protects you against someone who is using your computer and snooping through your browsing history. And someone with that kind of access to your computer could install a keylogger or other hidden program that records your keystrokes. Despite these limitations, private browsing can be a helpful way of reducing the amount of information that is recorded on your computer when browsing.
Resources:
Your Guide to Private Browsing | HuffPost Tech: menu commands and keyboard shortcuts to launch a private browsing session in IE, Firefox, Chrome, Safari, and Opera.
Private Browsing: Activating Private Browsing Mode in Your Favorite Browser | About: graphic tutorials on launching private browsing sessions in IE, Firefox, Chrome, Safari, Opera, and Flock; tips for private browsing on iPad, iPhone, and iPod touch.
Secure Browsing (through HTTPS)
How It Works: HTTPS is a way for users to protect the content of their communications from eavesdropping. When browsers don’t use HTTPS and transmit data openly, anyone along the path between the browser and the destination can view what is transmitted (that includes the ISPs that carry your traffic, or individuals surreptitiously intercepting the data). By encrypting the data, you make it much harder for anyone other than the intended recipient to see the content. Most major sites that require you to log-in (Google, Facebook, Twitter) and sites that transfer sensitive information (banking sites) now offer an encrypted connection. (Instead of http://www.google.com, your address bar will read https://www.google.com).
Limitations: Many sites don’t offer HTTPS, and some that do default to unencrypted HTTP or go back to unencrypted pages after the log-in process. Because of that, users must keep an eye on when they are encrypted and when they are not. Using a resource like HTTPS Everywhere can at least ensure that you connect using HTTPS for those sites that have that option. It’s important to remember that even if you connect to a site like Gmail using HTTPS, you are not hiding the destination only the content; an ISP or a government can still know you’re visiting Gmail. HTTPS is also not foolproof, as it is possible for a determined party to pretend to be the destination, in what is a called a man-in-the-middle attack.
Resources:
HTTPS Everywhere is a Firefox and Chrome extension from the Electronic Frontier Foundation. It will automatically switch sites from HTTP to HTTPS whenever possible and warn users about web security holes.
Circumvention & Anonymity
Among the greatest threats to Internet freedom are filtering and surveillance. These related issues either prevent you from accessing the content you want or allow third parties to keep track of what content you do access, respectively. Many of the tools to evade one also help with the other, so we discuss them together below. In most cases, these tools will help disguise your IP address, the sites you’ve visited, and technical information about your device, while possibly helping you access censored content.
Proxy Servers
How They Work: A proxy server is a machine that stands as an intermediary between your machine and the content you are trying to reach. Proxies can help evade censorship or filtering when connections to the proxy aren’t filtered but the desired content is. When you connect to censored content through a proxy, the censor will see only your connection to the proxy, not the verbotten content. Proxies also provide some anonymity because to the destination server, you look like you’re coming from the proxy server, not your actual origin. Web-based proxies are the easiest way to use a proxy server. Simply visit a proxy website with your prefered browser, enter your target URL, and the proxy site will then relay the request and deliver the site content back to you. There are also a number of downloadable clients for both Mac and Windows that connect your system to a proxy server.
Limitations: There are several downsides to using proxies, ranging from annoyances to serious security threats. On the annoyance side, because your data is passing through a single, fixed (and likely overloaded) point, it is not uncommon to experience slow load times and connection errors. On the security side, because all of your data is passing through a single, fixed point, it is easy for nefarious individuals to intercept any unencrypted data (using HTTPS or VPNs in addition to a proxy may address these concerns, but they have their own limitations described elsewhere in this post). In fact, sometimes hackers set up proxies with the express purpose of collecting user details, so it is important to carefully choose a trusted proxy. Using proxies can often be a game of cat and mouse; countries that filter sites often block known proxies, forcing users to move to a new, lesser known proxy. In some cases these same governments may create proxies specifically so they can monitor all the traffic and identify users.
Resources
Regularly updated lists of web-based proxies:
- Tech-FAQ’s (via CNET)
- Public Proxy Servers (via Open Security Research)
- Circumventor Central (via Open Security Research)
Web-based proxies (via Techlicious):
- Anonymouse
- HideMyAss
Downloadable proxy clients:
- Alkasir (Windows – English, Arabic) Learn more about Alkasir.
- Freegate (Windows – English, Chinese, Persian, Spanish) Learn more about Freegate.
- JonDo (Mac, Windows, Ubuntu, Linux, Android – English, German, Czech, Dutch, French, Russian) Learn moreabout JonDo.
- proXPN (Mac, Windows, and iPhone – English)
- Psiphon (Various configurations, including a lightweight web proxy that runs on Windows and Linux plus a cloud-based solution) Learn more about Psiphon.
- SabzProxy (Mac, Windows, Linux – Persian) Learn more about SabzProxy.
- Simurgh (Windows – English) Learn more about Simurgh.
- Ultrasurf (Windows – English) Learn more about UltraSurf. Also note Tor’s recent report detailing Ultrasurf security holes and Ultrasurf’s response.
- Your-Freedom (Mac, Windows, Linux – 20 languages) Learn more about Your-Freedom.
VPNs
How They Work: Like proxy servers, Virtual Private Networks (VPNs) route users’ traffic through their own servers. What makes VPNs different from a standard open proxy is that VPNs authenticate their users and encrypt data. Additionally, because of how VPNs are configured, they are more likely to work with software on your computer that you use for email, instant messaging, and “Voice over IP” (VoIP).
Limitations: VPNs share some of the same risks as proxy servers. Because all of your traffic is passing through a single point, your security is only as good as that of your VPN. Some VPN services keep traffic logs, and free services in particular may be disposed to sell your information to advertisers or turn it over under pressure from authorities. Free ad-supported VPNs may limit your bandwidth; paid VPN services are generally more reliable and come with a much higher bandwidth. It is important to keep in mind that the VPN provides a secure connection between you and the VPN, but not between the VPN to your ultimate destination. The use of HTTPS and other standard measures are still necessary to secure your connection your destination.
Resources
There are hundreds of VPN services online. What follows is a list of several popular services, both free and paid (via AnonymissExpress, How to Bypass Internet Censorship, and Techlicious.) View this wiki for a longer list of free and paid VPN providers, including monthly fees and technical characteristics. Note that some services are known to log IPs.
Free VPN Services:
- CyberGhost (English, French, Italian, German, Spanish)
- Hotspot Shield (English) Learn more about Hotspot Shield.
- VPN Reactor (English)
Paid VPN Services:
- AirVPN (English)
- Anonine (English, Swedish)
- Anonymizer (English)
- Banana VPN (English)
- IPREDator.se (English, Swedish)
- IVPN (English)
- LogMeIn Hamachi (12 languages)
- Perfect Privacy (English, French, German)
- Relakks (Chinese, English, Swedish)
- SecretsLine (English, French)
- SecurStar (English, German, Italian, Portuguese, Romanian)
- Steganos Internet Anonym VPN (English, French, German)
- StrongVPN (English)
- SwissVPN (English, French, German)
- Tiggerswelt (German)
- UnblockVPN (English)
- VPN Accounts (12 languages)
- VPN Gates (English)
- VPNod (English)
- Vpntunnel.se (English, French, German, Swedish)
- WiTopia personalVPN (English)
- XeroBank (English)
Tor
Tor (“The Onion Router”) is free, downloadable encryption software for online anonymity, recommended by the Electronic Frontier Foundation (EFF).
How It Works: Like proxies, Tor hides your IP address and location by routing your requests through another server. Tor, however, goes through multiple intermediary servers, a series of machines operated by volunteers all around the world. To the destination site, it looks like you are coming from the computer that was the last stop in the Tor journey, not from your computer. The Tor Browser Bundle works with Firefox and is available for for Mac, Windows, or Linux. It can also be stored on a memory stick for use on public computers.
Limitations: As with proxies, using Tor can be rather slow due to the number of servers between you and your destination. Furthermore, while data is encrypted between servers, it is unencrypted when the final server communicates with your destination. Those operating this “exit node” can see your log-ins, passwords, and other data (unless you have a secure “HTTPS” connection with the website you’re visiting), and it is “widely speculated that various government agencies and hacker groups operate exit servers to collect information” (Techlicious).
Emerging Technologies
Telex is a work-in-progress that is intended “to help citizens of repressive governments freely access online services and information.” The concept is this: when you request a website blocked in your country, Telex software on your computer changes your request to an allowed, decoy site. At the same time, it adds a hidden cryptographic tag to your request that only Telex can see. Telex will deploy boxes to locations along the Internet backbone and these boxes will use deep packet inspection to locate the cryptographic tag. The box will decode the tag to get your original intended destination, and will route your request to that site. Using that approach, Telex would enable people to access blocked content by making it appear that they are trying to access allowed content instead.
Sources and Further Reading
- Circumventing Internet Censorship from Open Security Research
- Five smart ways to keep your browsing private from CNET
- How to Browse the Web Anonymously from Techlicioius
- How To Bypass Internet Censorship from AnonymissExpress
- How to Bypass Internet Censorship (an ebook from howtobypassinternetcensorship.org)
- How to Surf the Web Anonymously from How Stuff Works
- Operation Encrypt Everything
- Protecting Your Security Online from Access
- The Surveillance Self-Defense Project from EFF
- Which VPN Providers Really Take Anonymity Seriously? from TorrentFreak


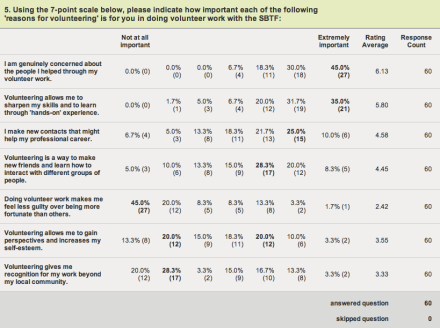
SBTF & USAID Partnership on Poverty Alleviation and Smarter Development
The Standby Volunteer Task Force (SBTF) continues to break new ground in. This time around we’re partnering with colleagues at the US Agency for International Development (USAID) who recognize, like we do, that equitable and sustainable economic growth is instrumental for countering extreme poverty across the globe. Being one of the biggest development organizations in the world, USAID has the resources to have significant impact on the livelihoods of millions. To this end, our colleagues want to better understand the link between their economic growth initiatives and their subsequent impact on poverty alleviation. This is where we as SBTF volunteers come in.
Our partners have access to a considerable amount of data which, if analyzed, will yield some very important empirical insights on the link between economic growth projects and poverty alleviation. The challenge, simply put, is to geo-code these datasets so that we can all better understand the geographic impact of various local economic initiatives vis-a-vis extreme poverty. Geo-code simply means finding the geographic location of said projects so that the resulting data can be mapped. USAID has already used automated methods to do this, but some datasets can only be processed by humans. But why map this data in the first place? Because maps can reveal powerful new insights that can catalyze new areas of potential collaboration with host countries, researchers, other development organizations and the public.
The local economic growth projects in question are aimed at reducing poverty and thereby changing people’s lives for the better. The results of the analysis, all of which shall be made public, will be used directly by USAID to fine tune their programs and thus increase their impact on poverty alleviation; welcome to Smarter Development! Given the extraordinary commitment of SBTF volunteers in projects past, our USAID colleagues have approached us to help them geo-code these important datasets. This is the very first time that USAID has reached out to online volunteer communities to actively help them process data about their organization’s impact in the field.
The result of this partnership will be a unique geo-coded dataset and a case study of said dataset that will be completely public for anyone to review. We’re excited to be partners in this effort since the project will demonstrate how crowdsourcing and online volunteers can play a significant role in both opening up development data and analyzing said data for the purposes of Smarter Development. This project will also provide SBTF volunteers with the opportunity to develop new skills while refining their existing skills and learning about how to work with new technologies.
Onwards!